Disk cloning and imaging, even under DOS with X-Ways Replica (forensically sound)
Examining the complete directory structure inside raw image files, even spanned over several segments
Native support for FAT, NTFS, Ext2/3/4, CDFS, UDF
Built-in interpretation of RAID 0 and RAID 5 systems and dynamic disks
Viewing and dumping physical RAM and the virtual memory of running processes
Various data recovery techniques and file carving
File header signature database, based on flexible GREP notation
Hard disk cleansing to produce forensically sterile media
Gathering slack space, free space, inter-partition space, and generic text from drives and images
File and directory catalog creation for all computer media
Easy detection of and access to NTFS alternate data streams (ADS), even where other programs fail
Mass hash calculation for files (CRC32, MD5, SHA-1, SHA-256, ...)
Unlike a competing product, does not depend exclusively on MD5 (collisions in MD5)
Powerful physical and logical search capabilities for many search terms at the same time
Manual NTFS decompression
Automatic coloring for the structure of FILE records in NTFS
Bookmarks/annotations
Bates-numbering of files
...
...and then some:
Support for the filesystems HFS, HFS+, ReiserFS, Reiser4, UFS, UFS2
Supported partitioning types: MBR, Windows dynamic volumes, GUID (GPT), Apple, unpartitioned (Floppy/ Superfloppy)
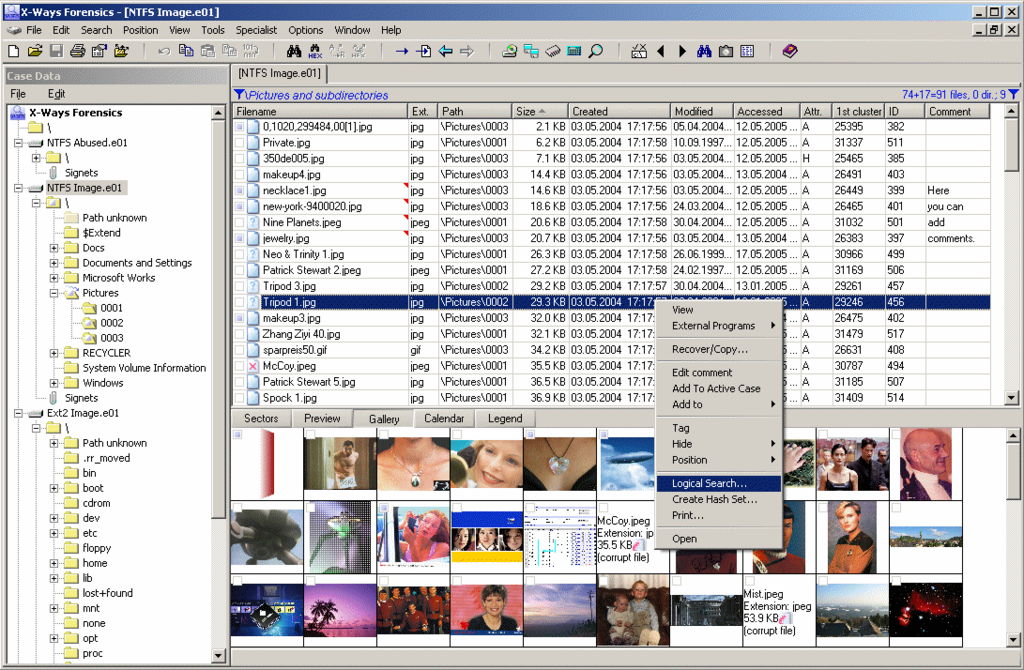
Gallery view for pictures
Calendar view
File preview, seamlessly integrated viewer component for 400+ file types
Keeps track of which files were already viewed during the investigation
Ability to examine e-mail extracted from Outlook (PST)*, Outlook Express (DBX), Mozilla (including Netscape and Thunderbird), generic mailbox (mbox, Berkeley, BSD, Unix), Eudora, PocoMail, Barca, Opera, Forte Agent, The Bat!, Pegasus, PMMail, FoxMail, maildir folders (local copies)
Automated file signature check
Write protection to ensure data authenticity
Complete case management
Automated activity logging (audit logs)
Automated reports that can be imported and further processed by any other application that understands HTML, such as MS Word
Ability to associate comments about files for inclusion in the report or for filtering
Ability to tag files and add them to customized report tables of notable items
Directory tree on the left, ability to explore and tag directories including all their subdirectories
Synchronizing the sectors view with the file list and directory tree
Powerful dynamic filters based on true file type, hash set category, timestamps, file size, comments, report tables...
Recursive view of all existing and deleted files in all subdirectories
Ability to copy files off an image or a drive including their full path, including or excluding file slack, or file slack separately or only slack
Automatic identification of encrypted MS Office and PDF documents
Finds pictures embedded in documents (e.g. MS Word, PDF, PowerPoint) automatically
Internal viewer for Windows Registry files (all Windows versions); automated Registry report
Viewer for Windows event log files
Lists the contents of archives directly in the directory browser, even in a recursive view
Logical search, in all or selected files/directories only, following fragmented cluster chains, in compressed files, optionally decoding text in PDF, WPD, ...
Powerful search hit listings with context preview, e.g. like “all search hits for the search terms A, B, and D in .doc and .ppt files below \Documents and Settings with last access date in 2004”
Search in both Unicode and various code pages
Logically combine search hits with an AND operator
Ability to export search hits as HTML, highlighted within their context, with arbitrary file metadata
Indexing and searching in an index, in Unicode or various code pages, unique in that it supports solid compound words
Skin color detection (e.g. a gallery view sorted by skin color percentage greatly accelerates a search for traces of child pornography)
Detection of host-protected areas (HPA), a.k.a. ATA-protected areas
Match files against the lightning-fast internal hash database
Ability to import NSRL RDS 2.x, HashKeeper, and ILook hash sets
Create your own hash sets
Ability to read and write evidence files (.e01 images), optionally with real encryption (256-bit AES, i.e. not mere “password protection”) and very flexible compression
Create report tables of relevant files
Ability to copy relevant files to evidence file containers, to pass on selected files to other investigators while retaining all metadata
Reduced and simplified user interface available for investigators that are not specialized in computers, at half the price: X-Ways Investigator...
This Archive Contains the following
X-Ways Davory Data Recovery v2.03
X-Ways Forensics v13.0 SR-1
X-Ways Security v1.3
X-Ways Trace v2.61
X-Ways WinHex v14.3
X-Ways Forensics v14.3 Manual.pdf
Can be run by double clicking the associated ".exe file in each archive or installed
by using the setp.exe file. This archive will updated soon with the Remaining X-Way programs.
Thank's for source by "jangkrikjr" with her post in Kaskus.us
Download The Program Here With 4shar1ng As Paswword







